What is the NIST Framework?
Cybersecurity is ineffective if everyone teaches it differently, each in their own language.
Having to re-learn different approaches and safety policies can be difficult for many employees without a technical background. Human error is the number one cause for cyber-attacks, often because employees didn’t fully understand the harm in actions such as weak passwords and phishing emails.
The U.S. National Institute of Standards and Technology (NIST) cybersecurity framework was created to eliminate the noise in understanding potential risks and implementing improved cybersecurity practices. Using NIST, official U.S. government agencies and billion-dollar companies such as J.P. Morgan Chase maintain a better understanding of how to keep an organization technologically healthy and have built an effective cybersecurity program for highly sensitive data.
NIST’s proven strength makes it attractive for all MSPs to learn and implement as they partner up with smaller companies, especially as malware attacks skyrocket to over 5.4 billion incidents a year.
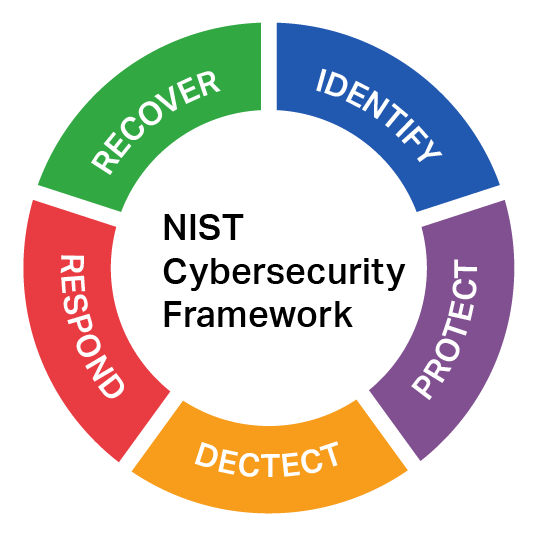
Breaking down the NIST Framework
Overall, there are 5 components to NIST, each containing categories and subcategories to organize and designate its main goal.
- Identify – What technology makes up your organization? Are there any broken or easily exploitable parts of your organization that a cybercriminal could exploit?
- Protect – Don’t wait, act now. Create a safety policy for every function and tool in your organization’s IT environment. This can include privacy and password policies.
- Detect – Monitor traffic for any unusual behavior and investigate if you spot it. Determine what level of response major threats will need, such as malware and unauthorized access.
- Respond – Contain and eliminate the threat found in the “Detect” component. Figure out how the threat happened and improve your policy and security measures to prevent any future incident.
- Recover – Notify whoever was affected by the incident, restore any damage to your IT environment, and improve any exploited weakness in your security measures.
How can I use the NIST Cybersecurity Framework (CSF)?
NIST’s website is dedicated to teaching MSPS and IT decision makers about the CSF and how to properly implement it. Refer to this website for any additional resources your IT partners may need if you’re considering adopting the CSF into your organization’s cybersecurity program.
If you don’t yet have an MSP but you’re still interested in adopting NIST’s CSF, ask about it when you’re interviewing potential partners. Because NIST is regarded as a “best practice” in the IT world, many MSPs seek out NIST certifications and will gladly talk to you about how they implement it in their cybersecurity programs.
If you or your IT partner are worried about it being “too late” to implement NIST’s CSF, know that there’s no better time to get started. This practice is specially designed to benefit organizations big and small and could be your company’s sole safeguard against the next wave of trending cyberattacks.
Want to learn more about cybersecurity practices that could save your business’s reputation? Visit our blog.