Cybersecurity Services
Securing Your Future: NIST-Based Cybersecurity in an Era of Rising Digital Threat
To keep you at the forefront of cybersecurity defense strategies and tactics, we follow National Institute of Standards and Technology (NIST) cybersecurity frameworks.
Is your technology secure?
- Do you have proof that implemented security tools and tactics are working?
- Do you know who has access to your data and devices?
- When was the last time your IT systems and data were backed up?
- Are you aware of the latest cyber threats targeting your industry?
- Do you have a plan in place for adverse events or security incidents?
If not, your organization is not sufficiently protected, period.
Beyond Outdated Standards: Embracing NIST for Cutting-Edge Cybersecurity Solutions
Last generation's cybersecurity tools are no longer enough to defend against the onslaught of cybercrimes.
The average total cost of a ransomware breach is $4.62 million. Not many small-to-medium-sized businesses can survive that.
Any organization that fails to align with NIST cybersecurity frameworks will be left behind. Don't get left behind. Learn more about NIST here.
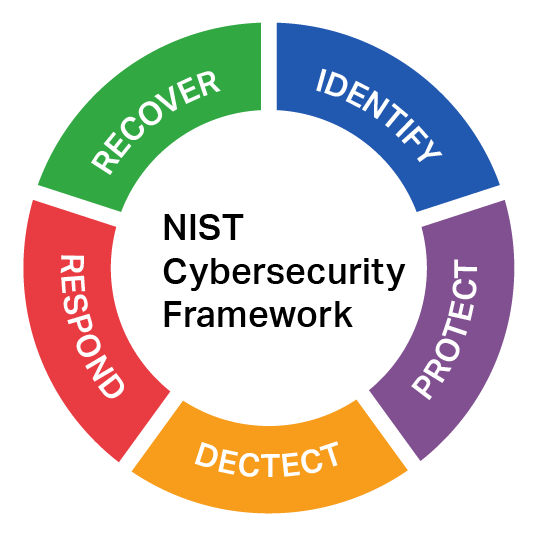
Cybersecurity Services Fortified by NIST Frameworks
Understand, focus, and prioritize your cybersecurity efforts based on your organization’s risks
- Assess your risk
- Strategize your risk response
- Manage your risk
Trust one of the leading cybersecurity companies to safeguard critical infrastructure and limit the impact of a cyberattack
- Defend your identity to keep outsiders out
- Educate your staff on the latest cyber threats
- Secure your data
- Protect your information
- Maintain your resources
- Guard your policies, procedures, and agreements
Quickly identify cybersecurity attacks that put your company at risk with data collection and analysis
Monitor, capture, and analyze your data to stay ahead of threat actors using:
- Endpoint Detection and Response (EDR)
- Network Detection and Response (NDR)
- Managed Detection and Response (MDR)
- Log Management
- Security Information and Event Management (SIEM)
Implement a Disaster Recovery Plan/Incident Response Plan (IRP) within the Business Continuity Plan (BCP)
Immediately and appropriately act to contain, eradicate, recover and capture lessons learned during a cybersecurity incident or adverse event.
An IRP will tell you how to:
- Determine critical network components and prioritize backups
- Identify and analyze the incident using logs and other data
- Map out mitigation activities needed
- Recommend improvements to prevent future incidents
Firmly Engage a Leading Cybersecurity Firm to Safeguard Your Organization's Resilience and Expedite Business Recovery
Your long-term recovery continues with:
- Business Continuity Plan (BCP)
- Disaster Recovery Plan (DRP)
- Realization of recommended improvements
Additional Resources for Businesses Seeking Advanced Cybersecurity Services
Though aligning with NIST is critical, you’ll also need Virtual Chief Information Security Officer (vCISO) advisory services to guide your organization to the best cybersecurity tools and tactics to meet its primary objectives.
Our cybersecurity partners
Ready for Cybersecurity Services That Keep Your Data and Your People Productive and Safe?
Contact us. Let’s protect your technology together.